How to Make a Keylogger in Python
Creating and implementing a
keylogger from scratch that records key strokes from keyboard and send
them to email or save them as log files using Python and keyboard
library.
A keylogger is a type of surveillance technology used to monitor and record each keystroke typed on a specific computer's keyboard. In this tutorial, you will learn how to write a keylogger in Python.
You
are maybe wondering, why a keylogger is useful ? Well, when a hacker
(or a script kiddie) uses this for unethical purposes, he/she will
register everything you type in the keyboard including your credentials
(credit card numbers, passwords, etc.).
The
goal of this tutorial is to make you aware of these kind of scripts as
well as learning how to implement such malicious scripts on your own for
educational purposes, let's get started!
Download source code
Download source code above
First onna need to install a module called keyboard, go to the terminal or the command prompt and write:
This
module allows you to take full control of your keyboard, hook global
events, register hotkeys, simulate key presses and much more, and it is
small module though.
So, the Python script will do the following:
- Listen to keystrokes in the background.
- Whenever a key is pressed and released, we add it to a global string variable.
- Every N minutes, report the content of this string variable either to a local file (to upload to FTP server or Google Drive API) or via email.
Let us start by import the necessary modules:
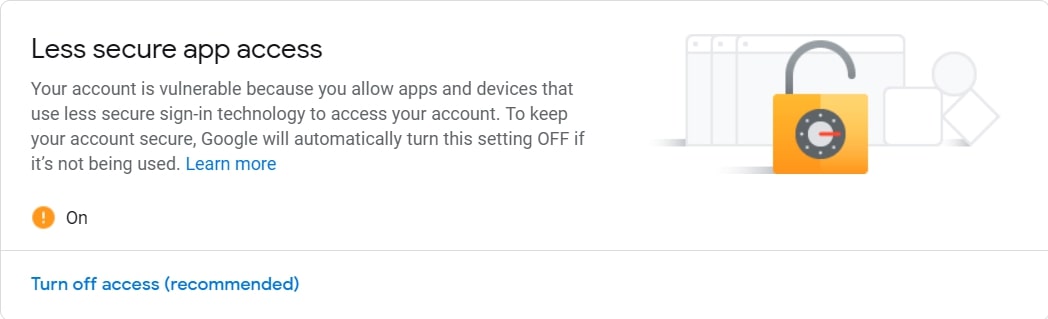
If you choose to report key logs via email, then you should set up a Gmail account and make sure that:
- Less secure app access is on (we need to enable it because we will log in using smtplib in Python).
- 2-Step Verification is off.
Like it is shown in these two figures:

Now let's initialize our parameters:
Note: Obviously, you need to put your correct gmail credentials, otherwise reporting via email won't work.
Setting SEND_REPORT_EVERY to 60 means we report our keylogs every 60 seconds (i.e one minute), feel free to edit this on your needs.
The best way to represent a keylogger is to create a class for it, and each method in this class does a specific task:
We set report_method to "email" by default, which indicates that we'll send keylogs to our email, you'll see how we pass "file" later and it will save it to a local file.
Now, we gonna need to use keyboard's on_release() function that takes a callback that for every KEY_UP event (whenever you release a key in the keyboard), it will get called, this callback takes one parameter which is a KeyboardEvent that have the name attribute , let's implement it:
So whenever a key is released, the button pressed is appended to self.log string variable.
If we choose to report our keylogs to a local file, the following methods are responsible for that:
The update_filename()
method is simple; we take the recorded datetimes and convert them to a
readable string. After that, we construct a filename based on these
dates, in which we'll use it for naming our logging files.
Then we gonna need to implement the method that given a message (in this case, key logs), it sends it as an email (head to this tutorial for more information on how this is done):
The method that reports the keylogs after every period of time:
So we are checking if the self.log
variable got something (the user pressed something in that period), if
it is the case, then report it by either saving to a local file, or
sending as an email.
And then we passed the interval (in this tutorial, I've set it to 1 minute or 60 seconds, feel free to adjust it on your needs) and the function self.report() to Timer() class, and then call the start() method after we set it as a daemon thread.
This way, the method we just implemented sends keystrokes to email or saves it to a local file (based on the report_method) and calls itself recursively each self.interval seconds in separate threads.
Let's define the method that calls the on_release() method:
For more information about how to use keyboard module, check this tutorial.
This start() method is what we'll use outside the class, as it's the essential method, we use keyboard.on_release() method to pass our previously defined callback() method.
After that, we call our self.report() method that runs on separate thread and finally we use wait() method from keyboard module to block the current thread, so we can exit out of the program by CTRL+C.
We are basically done with the Keylogger class, all we need to do now is to instantiate this class we have just created:
If you want reports via email, then you should uncomment the first instantiation where we have report_method="email". Otherwise, if you want to report keylogs via files into the current directory, then you should use the second one, report_method set to "file".
When
you execute the script using email reporting, it will record your
keystrokes, after each minute, it will send all logs to the email, give
it a try!
Here is what I got in my email after a minute:
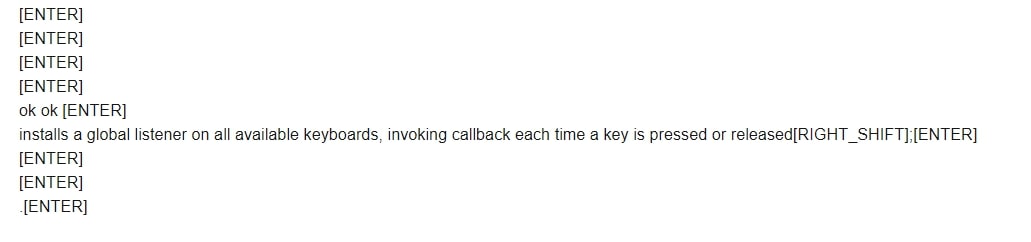
This was actually what I've pressed in my personal keyboard in that period !
When you run it with report_method="file" (default), then you should start seeing log files in the current directory after each minute:
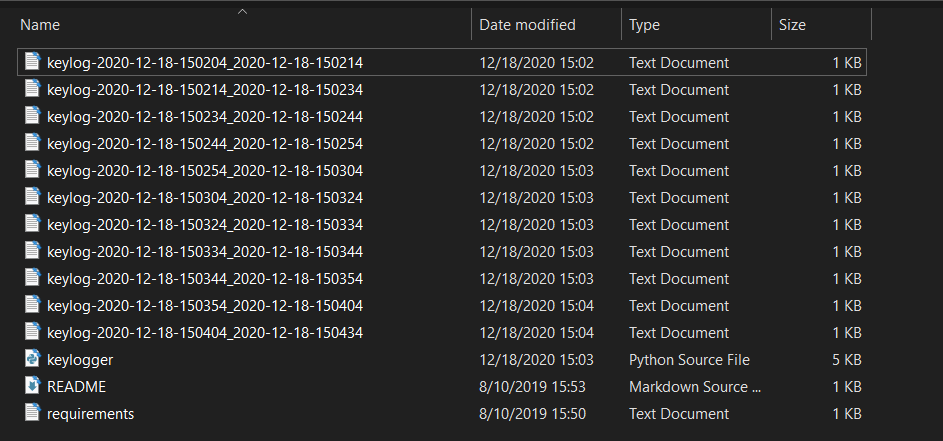
And you'll see output something like this in the console:
Conclusion
Now you can extend this to send the log files across the network, or you can use Google Drive API to upload them to your drive, or you can even upload them to your FTP server.
Also, since no one will to execute a .py file, you can build this code into an executable using open source libraries such as Pyinstaller.
DISCLAIMER: Note that I'm not responsible for using this code on a computer you don't have permission to, use it at your own risk!