Malicious QR Code with QRGen
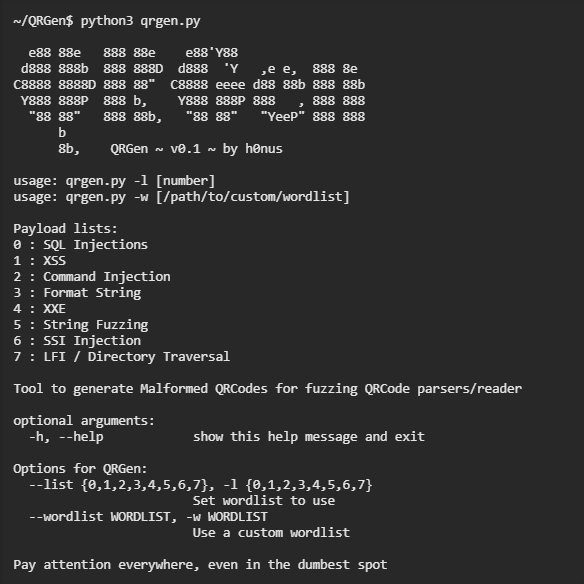
QRGen comes with a built-in library that contains lots of popular exploits, which is extremely useful if you have time to sit down with the same device you're looking to exploit and find out which one works. For a penetration tester looking to audit anything that uses a QR code scanner, merely buying the same scanner and running through the exploits can lead you to get the scanner to behave in unexpected ways. The categories of payloads available on QRGen can be accessed by using the -l flag and a number while running the script. The number and payload type are listed below.
Command Injection
Format String
String Fuzzing
SQL Injection
Directory Traversal
LFI
XSS
watch video
Install QRGen
To start with QRGen, we'll need to download the repository from GitHub do perform the command below in a terminal window.
git clone https://github.com/h0nus/QRGen cd QRGen pip3 install -r requirements.txtGenerate Malicious QR Codes from a Payload Type
After installing the packing, you can run the script by typing python3 qrgen.py as following −
To start, let's create a payload containing format string payloads. To do so, run QRGen with the following argument.
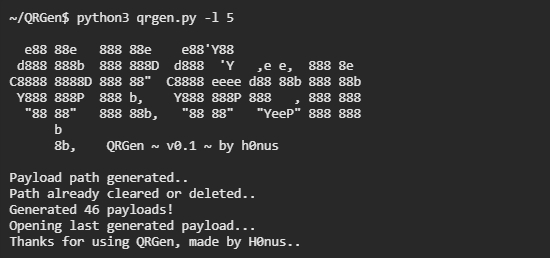
Finally, a series of QR codes will be generated, and the last one that was created will open automatically.

No comments:
Post a Comment